SSH is the most commonly used development tool if you have a remote machine, like a supercomputer or a PC in your office. Plentiful introduction to SSH can be found by search engine, like this one. So I will only record some basic moves commonly used.
Connect to an SSH server
SSH client is ready-to-use on modern Windows systems.
If you find that
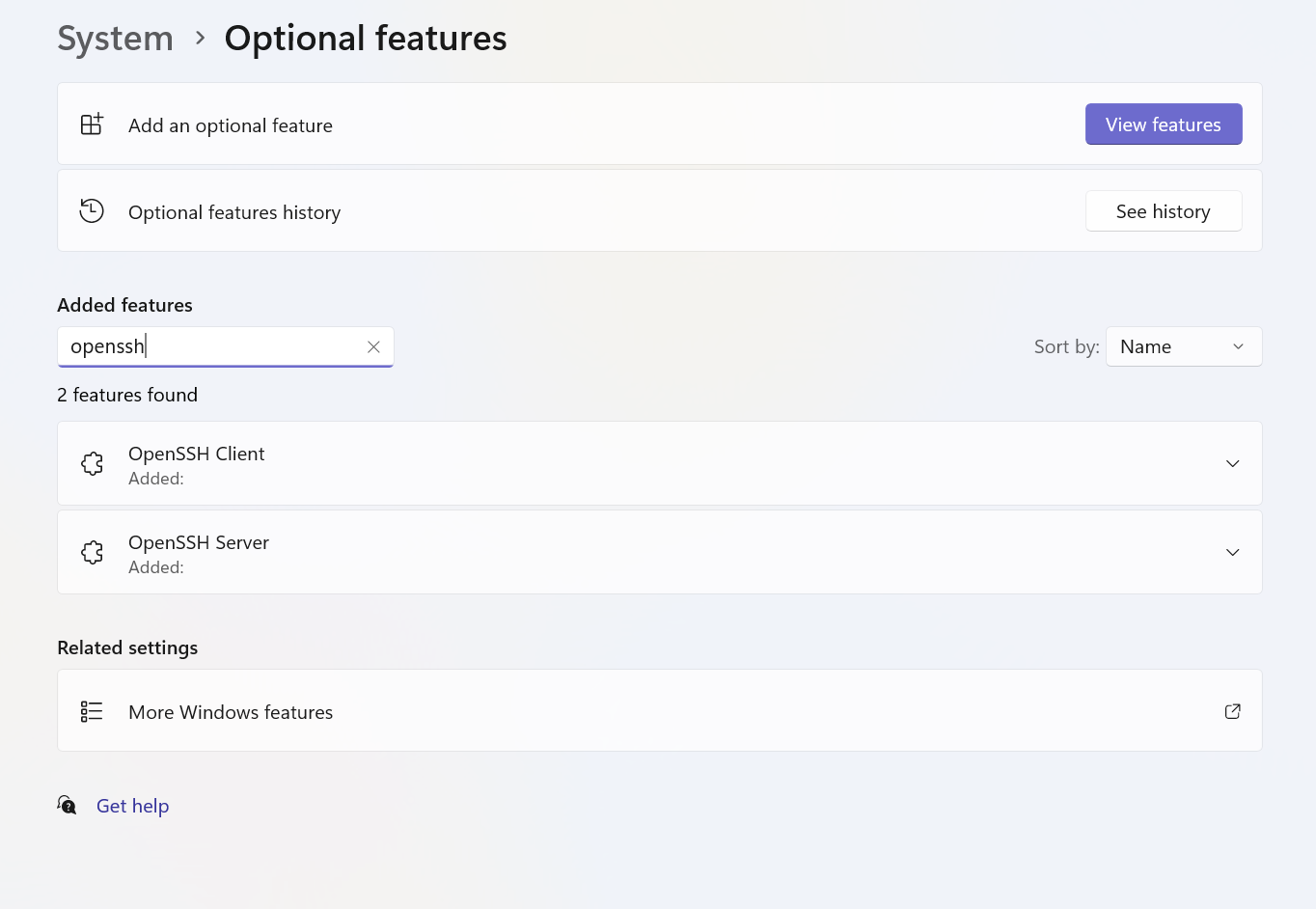
sshcommand is missing on Windows, for Windows 10/11, you should install it fromOptional Features:
Click on
Add an optional feature→View Featuresand findOpenSSH Clientand install.Make sure you can have output indicating the ssh executable’s path like
where.exe sshorwhich sshbefore you go on.
Suppose you are given a server with:
- hostname: 192.168.31.2
- user: harry
- password: pass-word
The username and password is same as the login information you use to log in that machine on the site. The hostname could be a domain name or raw IP like above. Meanwhile, sometimes the host service listens to another port other than default 22 port, say:
- port: 2345
You are supposed to be able to connect in your shell (of the client machine) with:
| |
The -p <port> can be omitted if the port is the ssh default 22.
Ssh client program ssh will prompt you to enter the password, then your shell is connected to the remote machine 192.168.31.2.
Entering the same command-line too often is inefficient, therefore we would like to give harry@192.168.31.2 a name “office”, suppose this connects to the computer in my office.
To record the ssh remote server login, edit the ssh configure file on your client machine ~/.ssh/config (Windows Also).
| |
After this, typing
| |
does the job.
SSH authentication with keys
You are not allowed to automatically enter the password. So, when connecting SSH with password, you must manually enter it in the console.
Sometimes it might be unsafe to use passwords and the server side forbids any password login.
So, you are supposed to use a pair of public-private keys as ssh’s authentication method whenever possible.
If you don’t have ssh key pairs, just run in your client machine’s shell:
| |
and press enter (using default parameters) when prompted until the end. Using non-default parameters will need extra configuration.
The parameter -t ed25519 chooses ed25519 as the signature algorithm. It is not recommended to use rsa, or you should actually avoid using rsa anymore, with the reason here.
After ssh-keygen, you have the key pair ~/.ssh/id_ed25519 and ~/.ssh/id_ed25519.pub. Remember only the .pub is the public key and is safe to show.
Then, you have to inform the ssh server of you public key to be able to connect without a password. Run
| |
to automatically do the key copying.
The tool ssh-copy-id is not found on Windows, so a manual copying is needed. Just run:
| |
on the client machine and copy the output and append it to ~/.ssh/authorized_keys on the remote (host) machine with:
| |
or any text editor you like.
After this, you should be able to simply ssh office to enter the remote shell.
Other parameters
| |
Port: Sets the port on the host machine to connect ssh. Default is 22.ServerAliveCountMax: This sets the maximum number of keepalive messages that can be sent without receiving a response.ServerAliveInterval: This sets the interval (in seconds) between each keepalive message.IdentityFile: Explicitly sets the private key to be used.ProxyCommand: Used to connect to proxy before connecting ssh, in this case, we use a SOCKS5 proxy at1.2.3.4:1080.
These parameters can be passed through -o option in command line.
For a complete reference, see Linux man page.
SSH server on Windows
If you have a Windows machine that you want to access by SSH, you can configure it to be an SSH server.
Before setting up a server, you should have a little network knowledge. See Making server visible to the Internet.
Install OpenSSH server
OpenSSH server feature and its service can be switched on by GUI or command-line on Windows. You can read this tutorial.
Here we have a simple GUI tutorial for Windows 11.
First, install OpenSSH. Search for features from the global search and choose the optional features in settings. Then select Add an optional feature and search for openssh:
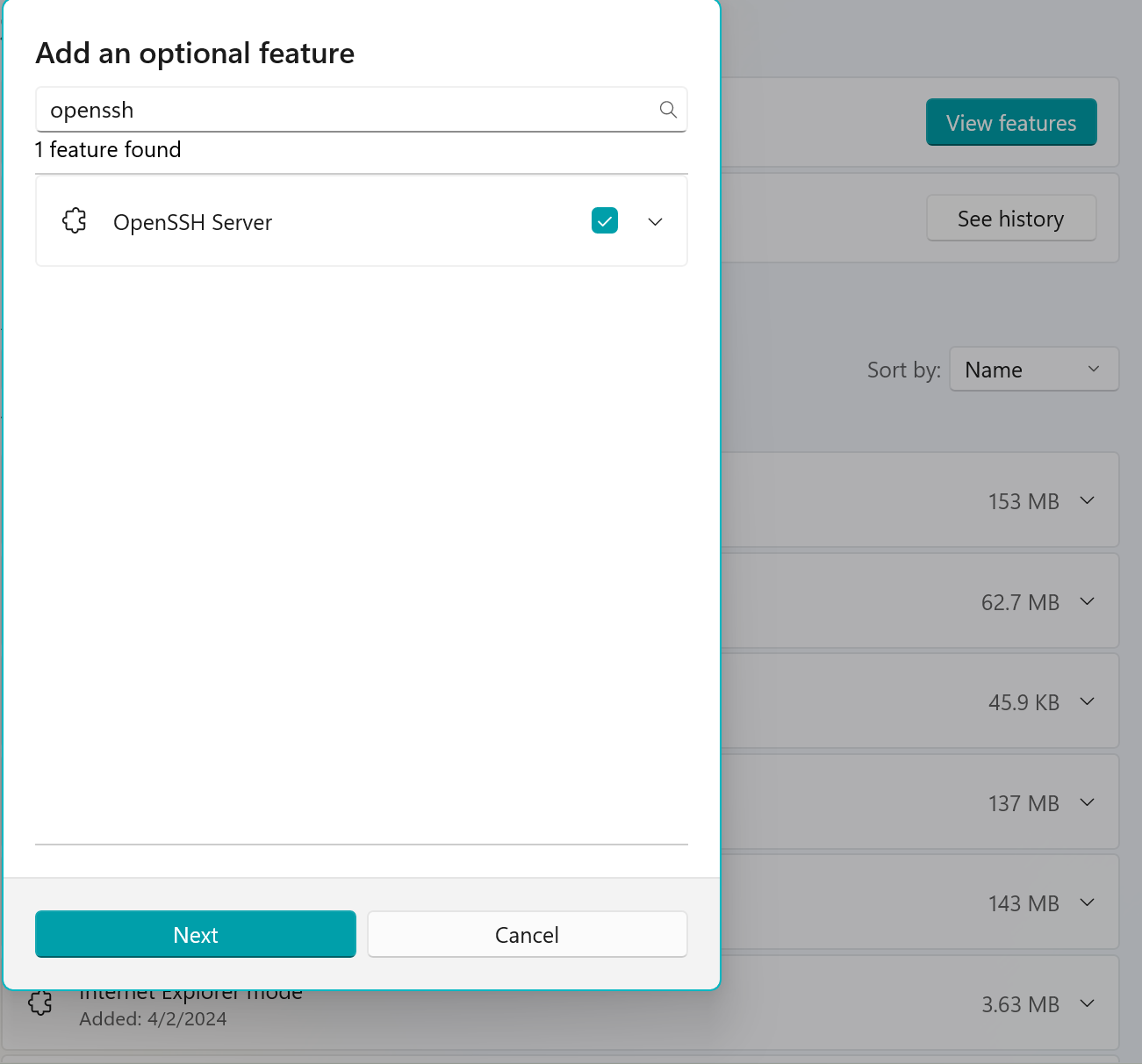
go through until the end and Windows will install OpenSSH:
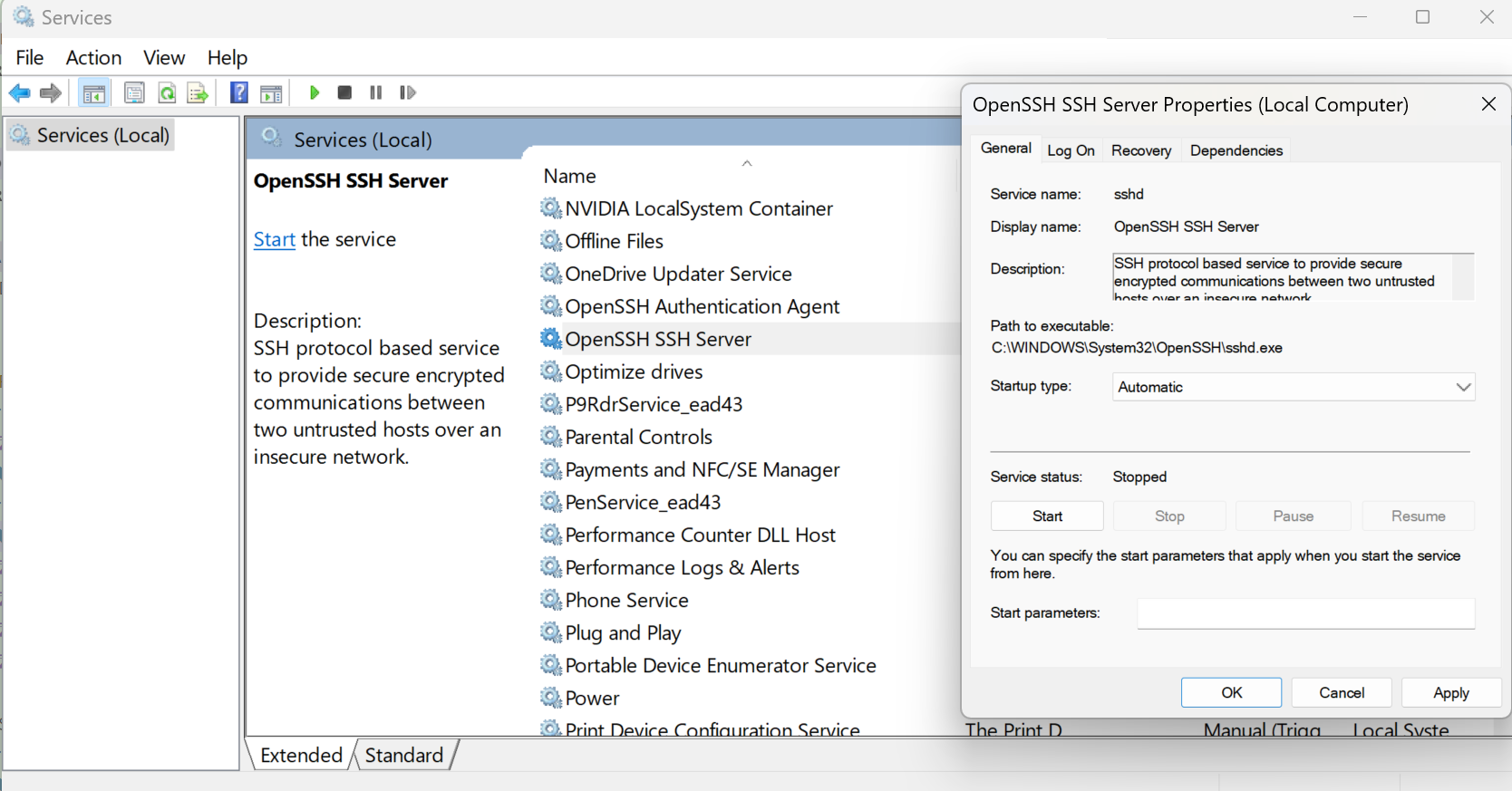
Start OpenSSH service
After OpenSSH is installed, go to services (run services.msc or search in the bar) and set OpenSSH SSH Server and OpenSSH Authentication Agent’s Startup type to Automatic and click OK. If they are not running, start them manually. They will start in the background automatically after next boot.
Using netstat in CMD will show if the service is listening to the 22 port:
| |
Using this in Windows PowerShell line will see the status of firewall rule:
| |
You can also test if ssh service is running by ssh to localhost:
| |
Substitute harry with your actual Windows local account username. The local account’s username is not the same as your Microsoft username, as shown in your Start page or Settings if you have logged in with a Microsoft Account. You can get your username by checking the path of you home directory. Usually, your home is in C:\users\<username>, and with localization like 简体中文 it could look like C:\用户\<username> in File Explorer. An easy way is to start a fresh Windows PowerShell or CMD to check the username.
You will be prompted to enter password, which is the password and not the PIN you use to log in your system.
If you can successfully log in through localhost, the ssh service is running.
The configuration of the service is in C:\Programdata\ssh\sshd_config by default, and within check the lines:
| |
to make sure key and password are allowed in the login process.
Remote SSH access
If you plan to remotely use your computer through SSH, inside or outside the local network, further checking is needed. You need to check the connectivity and use port forwarding + static public IP + static DHCP when necessary, see the server notes.
Firewall rules
You may find by default, ssh harry@localhost on the server runs fine, but doing this from any other machine inside or outside the local network gives a connection failure, which is most likely a result of firewall rules.
In the Windows Defender Firewall with Advanced Security panel’s inbound page, find the OpenSSH firewall rule we found earlier. Go to Advanced tab and check all the Domain, Private and Public profiles, to allow ssh inbound connections to the service from public internet. Click OK to save the changes.
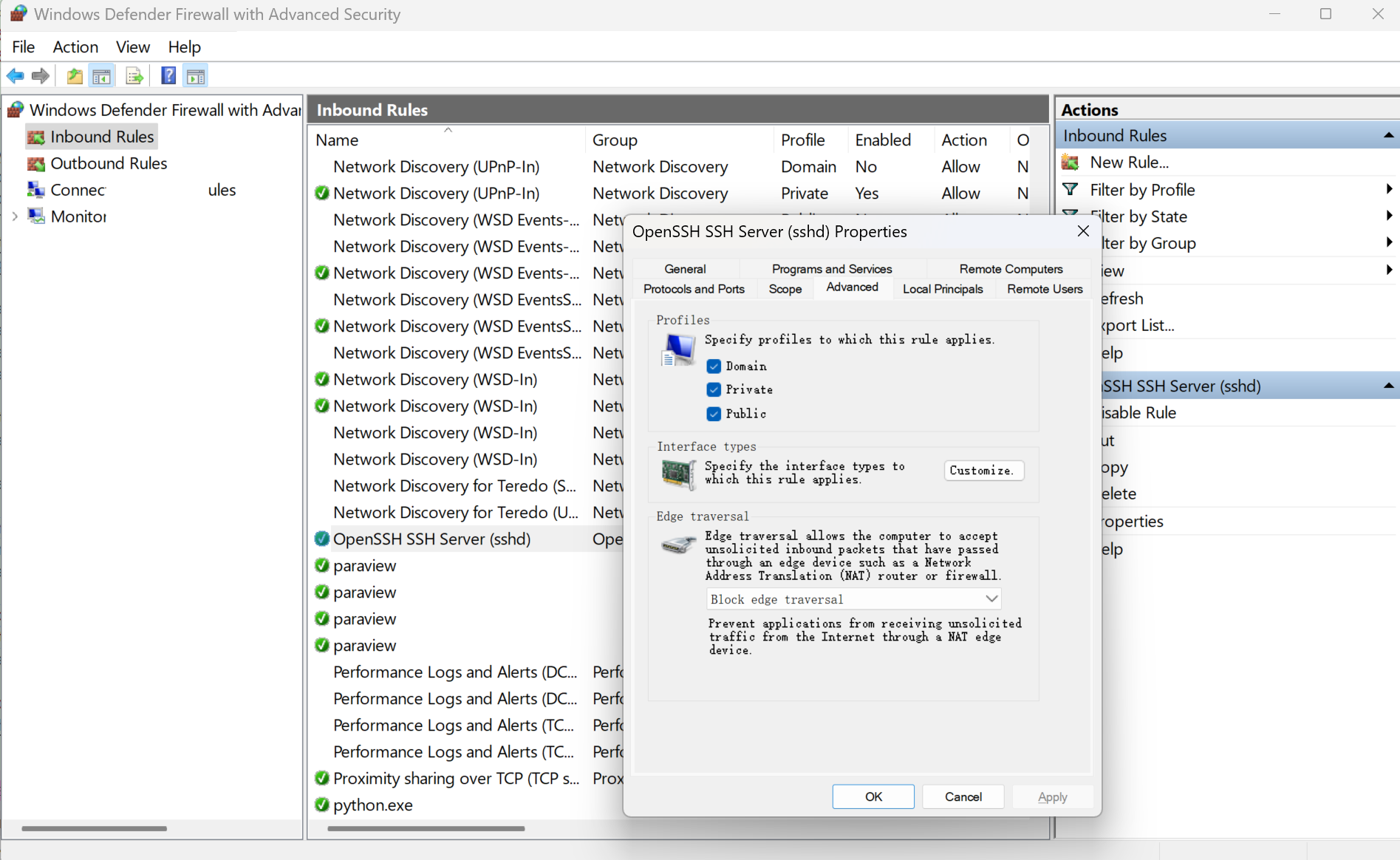
After updating the firewall rule’s profile type, try again and this mostly works.
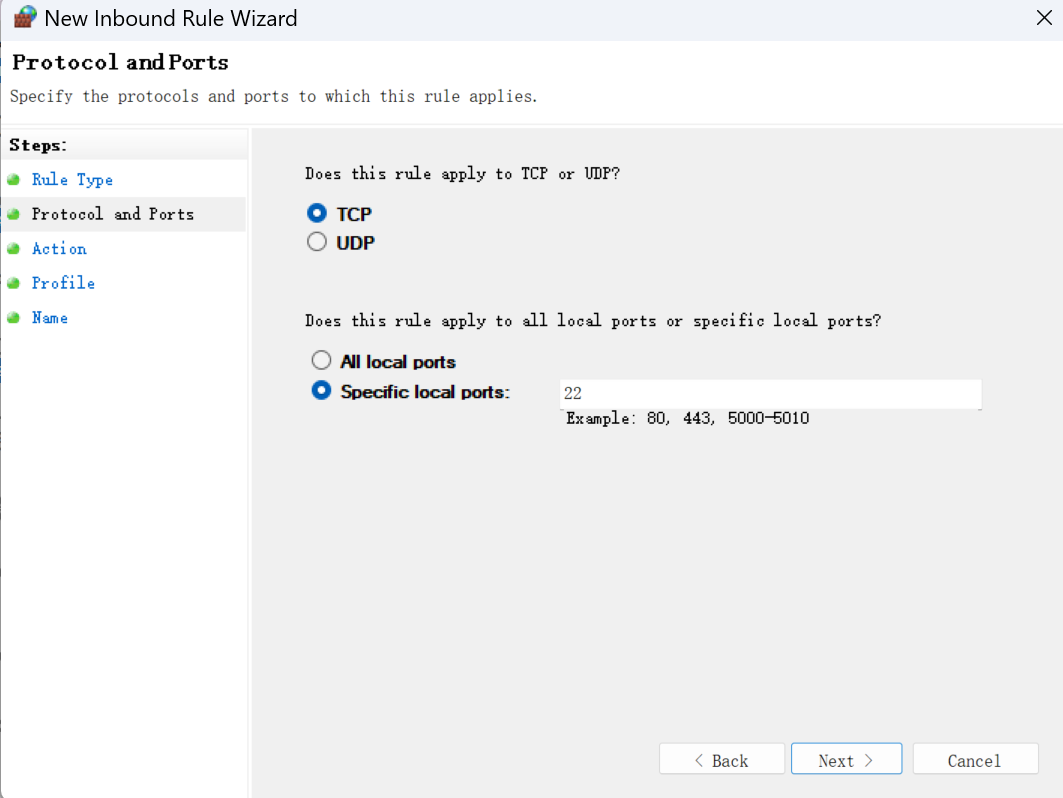
If an existing firewall rule is nonexistent or the method above did not work, try creating an inbound firewall rule in the Windows Defender Firewall with Advanced Security panel (I’m using the vanilla Windows Defender, other security solutions like 火绒 or Kaspersky might need different procedures to set the firewall). In the wizard, select Rule Type Port, select Protocol and Ports TCP and Specific local ports being 22. Action is Allow the connection. In Profile select all. Give a descriptive name like OpenSSH server inbound rule.
Key authentication of administrator
If your account is an administrator (which is the most case on Windows), you cannot log in through keys by simply adding your pubkey to ~/.ssh/authorized_keys. You also need to add them to C:\ProgramData\ssh\administrators_authorized_keys (create new file if not existent).